With the Panther log puller for CrowdStrike, teams can ingest CrowdStrike Falcon data, apply Python-based real-time detections, and search through historical data with SQL. Common security use cases for CrowdStrike and Panther include:
In this spotlight, we’ll highlight how you can leverage Panther to get additional value from CrowdStrike Falcon events and add an extra layer of analysis, real-time alerting, and investigation capabilities with long-term storage.
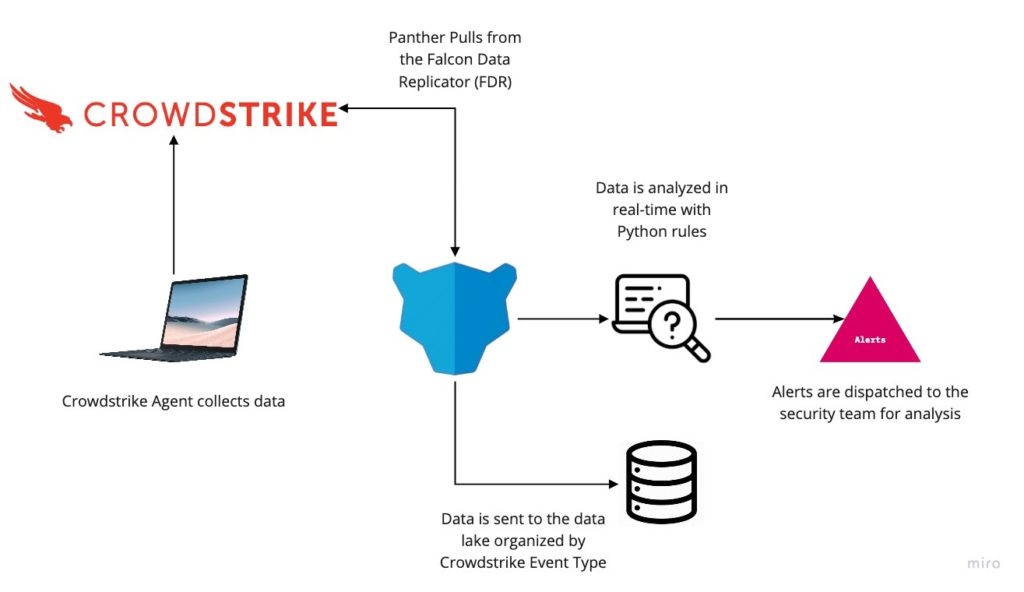
To get started, use Panther to collect CrowdStrike endpoint events by integrating with the CrowdStrike Falcon Data Replicator (FDR). For those that might not know, the raw event data generated by CrowdStrike is ingested into CrowdStrike ThreatGraph and used to detect sophisticated attacker behaviors by watching processes, network connections, and more.
The CrowdStrike FDR allows teams to push raw event data from CrowdStrike’s Platform to an Amazon S3 bucket. This way, your data can be ingested, transformed, analyzed, and stored alongside the rest of your security telemetry.
Panther extends CrowdStrike’s capabilities by ingesting and normalizing the data to make it easily searchable in order to investigate and understand the full scope of an incident. CrowdStrike stores the endpoint data temporarily, which can make it difficult to identify why an alert might have been triggered. This lack of visibility leads to gaps in the narrative and vulnerabilities in your environment. Panther enables you to utilize your aggregated CrowdStrike data and provides an additional layer of detection with real-time alerting.
Panther normalizes and stores CrowdStrike logs into a highly-scalable security data lake for long-term retention, making it possible to run analytics over large amounts of FDR data. This gives teams full end-to-end context of their environments, as well as the ability to run forensics, triage alerts, and identify suspicious activity to quickly detect, investigate, and respond to potential breaches.
When an alert is generated from the FDR data (or other logs), Panther will dispatch a notification to security teams to triage the alert in systems like PagerDuty, Slack, Jira, or Microsoft Teams. Simultaneously, the normalized FDR data will get pushed to a data lake, organized by event type (network connection, DNS query, process information, etc).
If you’re interested in learning more about how Panther extends your data lake, read what Snowflake CISO, Omer Singer, says about Snowflake & Panther, or check out the on-demand webinar “Replacing legacy SIEM with Panther & Snowflake.” (I don’t think you’ll regret it).
With Panther, teams can onboard CrowdStrike Falcon, analyze with Python, and query with SQL, allowing teams to better:
For example, CrowdStrike collects NetworkListen events such as:
{
"event_simpleName": "NetworkListenIP4",
"name": "NetworkListenIP4MacV5",
"aip": "205.71.189.87",
"aid": "919264958fc641d1ba0650e30300be14",
"event_platform": "Mac",
"timestamp": "2020-11-30 18:48:59.738",
"LocalAddressIP4": "127.0.0.1",
"RemoteAddressIP4": "0.0.0.0",
"ConnectionFlags": 0,
"Protocol": 6,
"LocalPort": 22,
"RemotePort": 0,
"ConnectionDirection": 2,
"p_any_ip_addresses": [
"0.0.0.0",
"127.0.0.1",
"205.71.189.87"
]
}Code language: JSON / JSON with Comments (json)To add a detection, for example, for Mac’s listening on local port 22, the following Python rule could be used:
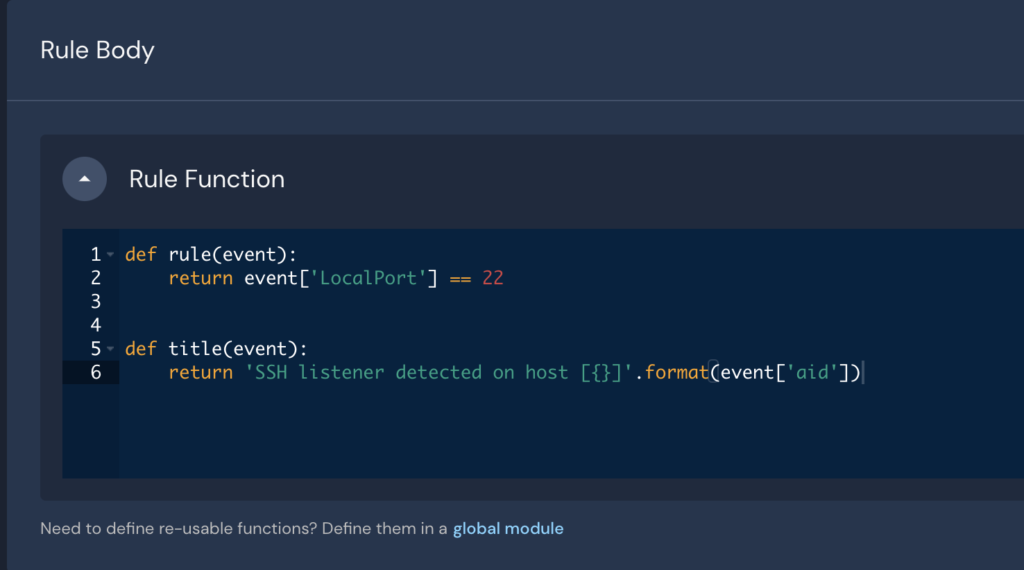
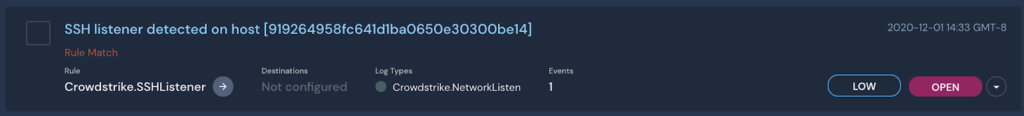
Resulting in the following alert:
These Python-based detections enable advanced analysis of events and add an extra layer of real-time security monitoring. But Panther can also be used to explore data to understand existing patterns in your fleet by using SQL.
To keep with the previous example, the query below will show all port 22 listeners that may have started in the past:
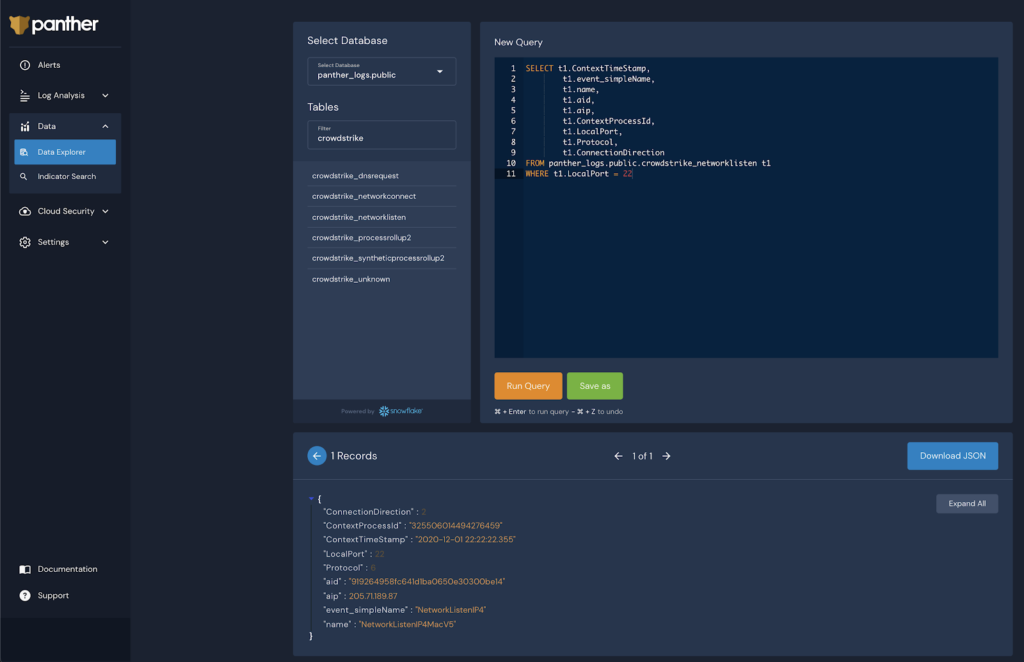
And because Panther has all of the CrowdStrike Falcon data in a single place, you can join other tables to understand the process which opened this network listener:
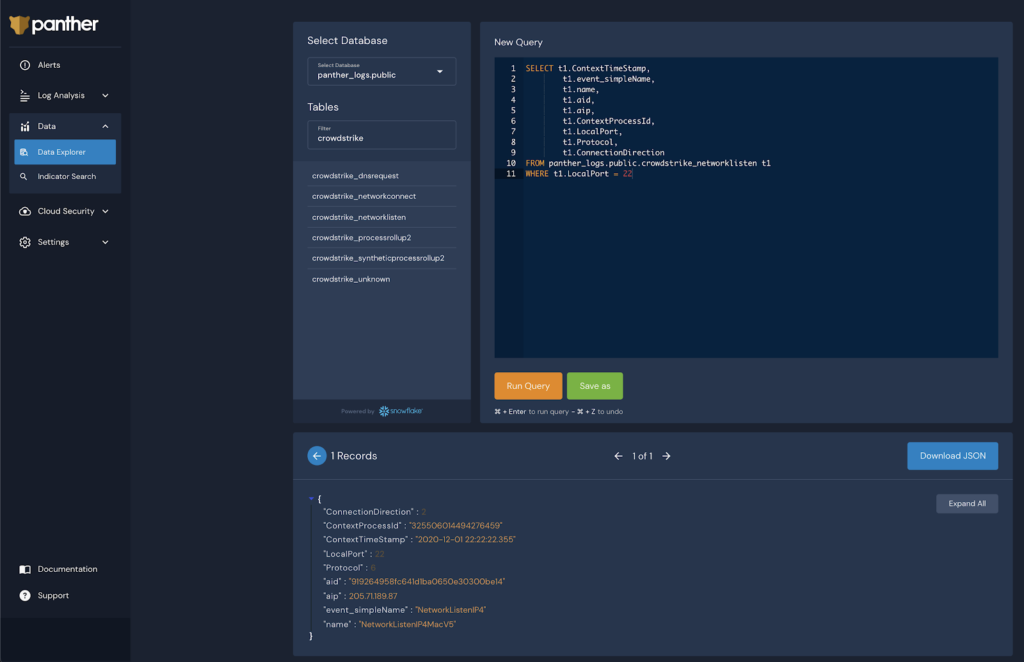
Teams love Panther because of the flexibility and customization possible with Python and SQL.
Get started building a modern detection and response program without the pains and limitations of SIEMs. Panther, a cloud-native security analytics platform, ships with pre-built integrations, such as CrowdStrike, to make it easy to quickly analyze your data, triage alerts, and remediate incidents using the tools and data you have.
To learn more about using Panther together with Crowdstrike, contact us for a demo of Panther Enterprise!
